2.5.2 Entity authentication
Entity authentication is the ability to assure one communicating party – using corroborative evidence – of both the identity of a second communicating party involved, and that the second party was actually active at the time the evidence was created or acquired [117]. This authentication type is also referred to as identification.
To achieve entity authentication, Alice and Bob typically engage in some kind of authentication protocol, which is a cryptographic protocol designed to achieve entity authentication.
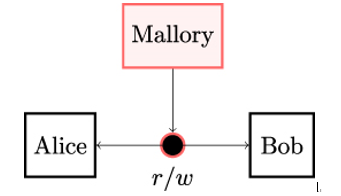
Figure 2.6: Entity authentication allows Bob to verify that the identity of the party he is communicating with is indeed Alice and that Alice is active during the identification. Malicious Mallory has the ability to read Alice’s and Bob’s messages and write arbitrary messages to the unsecured channel
In a typical example, Alice sends Bob a random, freshly generated challenge (for example, a random number) to which only Bob can respond correctly because Alice and Bob know a shared secret. After Bob has replied to Alice, he sends Alice a fresh, random challenge of his own and waits for the correct reply. If both replies from Alice and Bob are correct, the entity authentication is successful.
To prevent Mallory from compromising entity authentication by simply eavesdropping and replaying old messages, Alice and Bob need to verify each other’s authenticity in real time, with non-repeating challenges. This is referred to as timeliness or freshness. Hence, both parties must be active in the communication.
This protocol is an instance of mutual authentication because Alice and Bob authenticate each other. If only Alice or only Bob needs to provide the correct answer to a random challenge, then this would be an example of unilateral authentication.
The hack of remote keyless entry systems deployed in VW Group vehicles built between 1995 and 2016 and the attack on the Hitag2 rolling code scheme, are prominent examples of attacks due to insufficient entity authentication [71].
A Remote Keyless Entry (RKE) system is used to lock and unlock a car without having to insert a physical key. To do this, RKE systems transmit data from the remote control embedded in the car key to the vehicle.
After a button is pressed, a radio transmitter in the car key generates a signal in a public radio frequency band (for example, the 315 MHz band in North America and the 433 MHz or 868 MHz band in Europe).
The first generation of RKEs was based on a constant secret code and is therefore an instance of security by obscurity, a very dangerous anti-pattern in system design where the security of a system depends solely on the secrecy of its design. When the constant code is leaked once, the security of all vehicles relying on such an RKE is instantaneously broken.
The second generation of RKE systems relies on so-called rolling codes. In rolling codes, a counter value is increased upon each button press. The counter value – together with some additional input – is used to compute the next valid rolling code message, which is encrypted in the car key and sent to the vehicle.
The vehicle decrypts the rolling code message and compares the result to the last stored counter value. The counter value is accepted and the car is locked or unlocked if the received value is larger than the stored one. If the received counter value is smaller than the stored one, the attempt to lock or unlock the car is rejected.
However, researchers [71] discovered that RKE systems designed by VW Group are based on a worldwide master key. Because the key is identical for all affected cars, it can be extracted by inspecting the firmware of a single vehicle (which is exactly what the researchers did). Knowing that key allows an attacker to lock and unlock a car after eavesdropping on a single rolling code message.
Hitag2 is another widely deployed RKE that is not specific to a single car manufacturer. The counter in the Hitag2 rolling code is not a step-wise increasing value as it is based on the output of a stream cipher (see Chapter 4, Encryption and Decryption). An attack reported in [71] requires Eve to eavesdrop on merely four to eight Hitag2 rolling codes and allows her to recover the cryptographic key in approximately one minute. With that, the attacker can create a clone of the original remote control.
These attacks work because the RKE systems lack a cryptographically secure entity authentication. When the car receives a rolling code, it has no means to verify that it is indeed communicating with the right car key and that the car key is active during the communication.
