2.4 Integrity
Integrity is the ability to detect data manipulation by unauthorized entities. By data manipulation, we mean unauthorized acts such as the insertion, deletion, or substitution of individual data chunks or entire messages. It is not required that manipulations as such are rendered impossible; given the multitude of possible communication channels, this would be an impossible task. Clearly, a passively eavesdropping attacker such as Eve does not have the capability to perform data manipulation. We, therefore, assume a more active attacker named Mallory who also has the capability to write on the communication channel (see Figure 2.4).
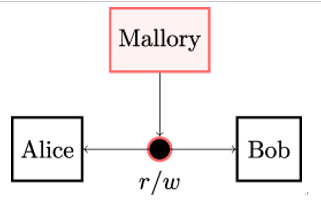
Figure 2.4: The malicious attacker Mallory has the capabilities r,w to read all messages sent between Alice and Bob and to write on the unsecured channel. Mallory’s goal is to manipulate the messages in a way that is not noticed by Alice or Bob
At first glance, one might be tempted to think that a good encryption function should be able to provide both confidentiality and integrity when applied to plaintext. After all, if Mallory cannot see the plaintext and has to blindly manipulate the ciphertext c coming from Alice, this should be noticed by Bob, as decryption will fail to produce meaningful plaintext. While this is true in most cases, there are certain ways to encrypt where Mallory has a fairly good chance of getting away with her manipulations, for example, stream ciphers or the Electronic Codebook Mode (see Chapter 4, Encryption and Decryption and Chapter 14, Block Ciphers and Their Mode of Operation, respectively).
The real reason for keeping confidentiality and integrity separate from security services using different mechanisms goes deeper, however. There are many situations where integrity is needed but confidentiality is either not needed or even not wanted. A good example is provided by the header of an IP packet. Among other data fields, it contains the IP address of the recipient of the packet. While it is a good idea to provide integrity protection of the IP header (the IPSec protocol does just that), confidentiality would be counterproductive since intermediate gateways need to see the recipient’s address to route the packet.
Attacks on the integrity of data can have severe consequences if they go unnoticed: important decisions might be based on wrong information, software systems might exhibit strange, inexplicable errors, and hardware-based systems could be physically damaged. A recent example of a data integrity attack is provided by the Stuxnet worm [106], allegedly composed in a joint effort by the NSA and the Israeli secret service Mossad to harm the Iranian nuclear program. Building upon a complex series of different attack vectors, Stuxnet finally managed to get access to the control software for centrifuges used to enrich uranium in Iranian nuclear facilities. By altering the control parameters, the centrifuges were made to run at a slightly higher speed than allowed and were rendered useless after a few months. Because of the long-term character of the attack, the real reason for the centrifuge failure was not detected for quite a long time.
Integrity can be achieved in a manner that is similar to detecting transmission errors in networking; basically, a cryptographic checksum hK is computed over the data m that Alice wants to protect and appended to her message m. If Bob receives a message (m,hK(m)), he can compute a checksum of his own over m. If this checksum does not equal hK(m), something has gone wrong: either there were transmission errors or someone has tampered with m.
Again, a secret parameter k has to go into the computation of the checksum. Otherwise, an intelligent attacker would be able to modify m to m and alter the checksum so that it fits the modified m. Moreover, a checksum designed to detect transmission errors such as the Cyclic Redundancy Check (CRC) in networking will not be enough, as they can be easily forged even without knowing the secret k. Instead, one has to use secure hash functions, as discussed in Chapter 11, Hash Functions and Message Authentication Codes.
