3.6 Key establishment
To communicate securely, Alice and Bob need to share the secret key in advance. According to [117], Def. 1.63, ”key establishment is any process whereby a shared secret key becomes available to two or more parties for subsequent cryptographic use”.
In principle, Alice and Bob might meet in person in a cafe and establish a shared secret. However, apart from the logistic problems, this approach does not scale very well: in a group of n people, each possible pair needs to establish a key of its own. As there are pairs, 100 people would need about 5,000 personal meetings. Obviously, an automated method of key establishment is in order.
Key establishment is a broad term in which we can further distinguish between key agreement and key transport. In a key agreement protocol, both parties involved have an influence on the final result, which is a shared key. The DH key exchange protocol mentioned in the first chapter is a prime example of a key agreement protocol. In a key transport protocol, on the other hand, one party (usually Alice) generates a key and sends it to Bob in a secure way.
3.6.1 Key transport
Key transport is a key establishment process in which one participant (Alice) selects the key, encrypts it, and distributes it to the other participant (Bob) [132]. Alice may generate the key herself or acquire it from some other source.
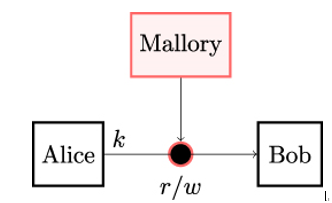
Figure 3.2: In key transport, one party (Alice) generates the secret key k and securely transmits it to another party (Bob). The transmission is done over an unsecured channel where an active attacker Mallory can read and manipulate data
Key transport can be performed using both public-key (or asymmetric) cryptography as well as with symmetric cryptography. If public-key cryptography is used, Alice encrypts the key to be transported using Bob’s public key and sends this information to Bob. Bob then decrypts the data received with his private key.
NIST Special Publication 800-175B [14] provides an example of a public-key cryptography-based key transport. Bob, the receiving party, is required to have a public-private key pair that can be used for the key transport. The transport is accomplished in two steps:
- Alice acquires an authentic copy of Bob’s public key PKBob, generates a symmetric key k to be transported, encrypts k using Bob’s public key, and sends the result c = EPKBob(k) to Bob.
- Bob uses his private key to decrypt the ciphertext, thereby obtaining the key k (optionally, Bob confirms the key reception to Alice to ensure that they both now have the same key).
If Alice and Bob want to use symmetric cryptography instead, there must be a long-term secret Kthat they have already shared somehow. From K, both can derive a Key-Encrypting Key (KEK) on a regular basis. To transport a session key SK to Bob, Alice encrypts it with KEK and sends the result to Bob. Bob now uses KEK to decrypt and retrieve the session key.
