2.5.1 Message authentication
Message authentication is the ability of the communicating party that receives a message to verify – through corroborative evidence – the identity of the party that originated the message [117]. This form of authentication is also referred to as data origin authentication.
Message authentication can be achieved by providing additional information together with the message. This information can be used by the receiving party to verify the identity of the party who sent the message – at least, this is true for asymmetric authentication protocols. In symmetric message authentication, we can only verify that a message was sent by someone in possession of the shared key (see also Chapter 5, Entity Authentication).
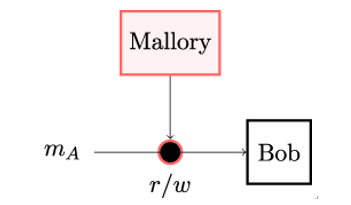
Figure 2.5: Message authentication allows Bob to verify that the message mA he receives has indeed originated from Alice, despite malicious Mallory having the ability to read Alice’s messages and write arbitrary messages to the unsecured channel
While message authentication ensures the origin of the message, it typically provides no guarantee of freshness. That is, with message authentication alone, it is not possible to say when the message was sent, only to verify its origin. As an example, imagine that Alice sends a message mA to Bob today, but Mallory intercepts that message and deletes it from the unsecured channel. Mallory could then re-send mA to Bob any time later, yet Bob would not be able to recognize that the message is delayed and is actually coming from Mallory rather than Alice.
The inability to determine whether a message is delayed or received out of order enables so-called replay attack, in which an authenticated message is sent a second time to the receiver, or reflection attacks, where an authenticated message is sent back to the sender. More details are given in Chapter 19, Attacks on Cryptography.
The lack of proper message authentication is the main cause for the notorious false base station attacks, which could originally be launched against 2G mobile networks and, because of the need for backward compatibility, also against 3G and 4G networks [143]. In these attacks, Mallory sets up a False Base Station (FBS), basically an antenna sending out a strong signal designed to lure mobile phones to connect to the FBS. The FBS then sends a standardized message to the phone to the effect that it does not support encryption. Therefore, the phone resorts to sending its speech data in plaintext to the FBS. If the phone is able to verify if the NullEncryption message is really coming from a legitimate network operator, the attack becomes infeasible.
Many other examples of attacks resulting from a lack of or faulty implementation of message authentication could be given. For example, email-based phishing attacks are only possible because email messages are not authenticated in most cases.
Message authentication is strongly related to integrity protection. After all, if Mallory modifies a message mA coming from Alice to some mA, thus breaking integrity, one might also argue that mA really is a new message coming from Mallory, but pretending to come from Alice. Therefore, one can say that message authenticity implies integrity.
