2.1 Technical requirements
This chapter introduces basic definitions, design principles, and goals and therefore requires no specific software or hardware.
2.2 Preliminaries
The fundamental objective of cryptography and computer security in general is to enable two persons, let’s call them Alice and Bob, to communicate over an insecure channel so that an opponent, commonly called Eve, cannot understand or unnoticeably alter their messages [168]. Alice, Bob, and Eve can also be referred to as (communicating) entities or parties and may be people or machines. Alice and Bob are either a sender or receiver, that is, a legitimate transmitter or intended recipient, of the messages. Eve is an adversary, an entity that tries to compromise the information security between Alice and Bob.
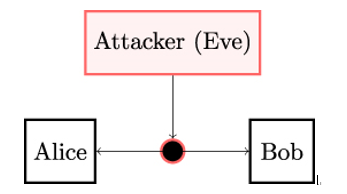
Figure 2.1: Legitimate communicating parties Alice and Bob transmit and receive information over an untrusted channel
Let’s clarify terms by looking at some definitions:
- An insecure or untrusted channel is a channel an opponent, or attacker, can access. The capabilities of the attacker (that is, what the attacker can or cannot do on the channel) may vary and are part of the so-called attacker model.
- A passive attacker is an attacker who is only able to read information from an untrusted channel. In contrast, an active attacker is an attacker who can also insert their own information, or alter, replay, reorder, or delete the information on an untrusted channel.
Figure 2.2 illustrates the two fundamental attacker models in cryptography. Cryptographers use the attacker model to express the assumptions about the power of the adversary, that is, the actions the attacker is assumed to be able to take as well as their computational power.
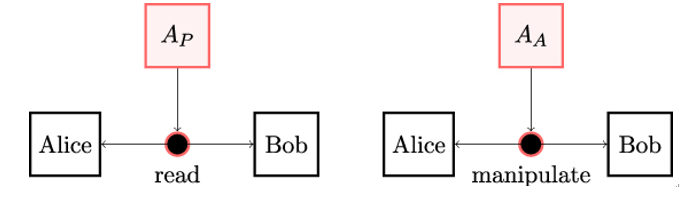
Figure 2.2: The two fundamental attacker models used in cryptography
The channel might be anything from a telephone line to a Wi-Fi network or satellite communication, and the information being sent from Alice to Bob can have an arbitrary structure – it might be numerical data, text, or simply some random blob. In computer science, blob, or binary large object, refers to a collection of binary data such as images, audio, or multimedia objects, or binary executables.
In numerous real-world applications, machine-to-machine or application-to-application communication needs to be secured. In this case, Alice could be equivalent to a web browser and Bob to a web server. Alternatively, Alice could be equivalent to an embedded device that is connected to the internet and Bob could be equivalent to a backend service the device is connected to.
Alice and Bob might even be the same person or entity, for instance, an electronic device. In this case, Alice is transmitting the information to her future self, that is, she wants to store the information securely.
Sometimes, Alice and Bob might engage in something called a cryptographic protocol, for example, to establish a key in a secure way, or in order to make sure they are really communicating with the correct entity. Here are precise definitions:
- A cryptographic protocol is a distributed algorithm defined by a sequence of steps that precisely specifies the actions required of two or more entities to achieve a specific cryptographic goal [117]. Transport Layer Security, one of the main topics of this book, is a cryptographic protocol for establishing a secure channel between Alice and Bob.
- In contrast, a cryptographic mechanism is a more general term referring to protocols, algorithms – specifying the steps followed by a single entity – and non-cryptographic techniques [117] such as trusted execution environments and role-based access control to achieve specific security objectives.
So, cryptographic mechanisms (and protocols among them) are tools with which Alice and Bob seek to achieve security objectives. But what precisely are these security objectives? There are several of them, and in the next three sections, we will explore the three most important ones.
